A foundational use case of Archive360’s Data & AI Governance Platform.
Digital Communications Governance and Archiving
Reduce the time, effort, and cost of capturing and governing communications across email, chat, meetings, and modern channels - for compliance, eDiscovery, supervision, and risk reduction.

Dedicated tenant. Your keys. Your controls. Audit-ready proof.
Centrally Archive, Compliantly Manage, and Quickly Access High Volumes of Communications Across Channels
6 Million
Messages/day continuously captured by Top 3 consulting firm1 Governance Model
To manage communications obligations: legal, regulatory, operational
4 Million
Emails/day continuously captured by Top 3 U.S. health insurance company
Proactively Manage Digital Communications Risks
Empower your teams to search, review, and manage large volumes of communications data compliantly, efficiently and cost-effectively.
Organizations face a growing number of communications channels, stricter regulatory expectations, and rising privacy and security requirements. Compliantly collecting, retaining, supervising, and producing communications data at scale is increasingly difficult without enforceable policy and audit-ready evidence. Archive360 brings communications from modern applications and legacy email archives into one governed layer - so your teams can search, review, manage, and prove outcomes efficiently.
- Ensures the right data is captured and managed, to meet regulatory obligations
- Consistently apply classification, entitlements, retention, legal, hold, and disposition
- Reduces storage and administration costs, freeing up operational space and IT resources.
- Reduces cybersecurity, data privacy, preservation, and compliance risks
- Provide cross-system visibility and control over retention, disposition and legal holds
- Accelerate eDiscovery with advanced search and refinement across multiple channels
- Provide case management, tagging, and annotation capabilities
- Ensure defensibility with a complete audit trail and proof of disposition
Unified Governance of Data From Communications Channels

What Communications Data Can I Archive?
Email, chat, meetings, mobile messaging, rich media, and other modern channels -captured and governed under consistent policy.
THE CHALLENGE
Digital Communications Risks and Compliance Costs are Increasing, but Your Tolerance and Budget are Not
The risk and cost of maintaining the status quo are no longer sustainable.
Compliance as an Afterthought
As the means of communicating and collaborating online have expanded from email to virtual meetings, chats, social media, instant messaging, podcasts, videos, and more, organizations contend with a growing volume and variety of data, a more-critical regulatory environment focused on data privacy, security, and sovereignty, and implementing a digital communication governance program that effectively meets the compliance requirements after the systems have already been deployed.
Ecomm Channel Proliferation
With an ever-increasing number and variety of digital communication channels, Organizations can no longer continue to have digital communications trapped in isolated repositories and expect system administrators to consistently and cost-effectively manage them according to policies. Each tool has different data management and search capabilities, making the enforcement of data governance policies, response to data requests, and audit of the data governance program complex, error-prone, and costly.
Data Over-Retention
The easiest, and many incorrectly assume safest, approach to managing data is to retain it all. The increased likelihood of a data breach, regulatory fines, and appearing in the headlines for the wrong reasons have amplified the risk of data over-retention and is forcing organizations to understand when data risk outweighs value so it can be appropriately managed and disposed.
THE SOLUTION
Digital Communications Governance and Archiving
Efficiently and cost-effectively meet your data management compliance, legal, and business objectives.
Policy-Driven Compliance
and Savings
Automatically capture and archive communications from operational systems and channels - so classification, entitlement, retention, supervision, preservation/legal hold, and disposition policies are enforced consistently and efficiently. Take the data management burden off content owners and IT support and increase productivity, reduce costs, mitigate risks, and drive better business decisions.

Accelerate Data Discovery at Scale
Quickly find relevant communications you are entitled to see in a single search across petabytes of data aggregated from multiple systems. Archive360’s unique class-based data architecture and advanced search/refinement capabilities enable fast and efficient searches across diverse data sets. When interactions happen across multiple channels such as email, Slack and Zoom, you can see the entire conversation in context as a topic originally raised in email is further discussed over a week in Slack and Zoom.
- Metadata-only indexing for faster, more cost-effective results
- Full content indexing where needed
- Exact match, any term, proximity, spelling variations, search within search
- Preview 100+ formats

Defensibly Manage Data
Data can be stored in the correct geolocation to ensure data sovereignty compliance and on immutable (WORM) storage to prevent tampering and ensure authenticity. All interactions with archived data, including metadata, disposition approval workflows, and retention overrides, are logged to provide a complete audit trail and audit-ready evidence - including proof of disposal - so legal and compliance teams can demonstrate policy enforcement and authenticity.

Unmatched Options for Protecting Your Data
Security by design and default
True Zero-Trust Security
Although many applications claim to follow zero-trust, least privileged principles, the fact is some “privileged users” have full access to all their features, functionality, and data. A compromised privileged user account is the most common point of entry leading to a data breach. By archiving data to Archive360, you remove privileged user access to the data. Even Archive360 administrators don’t have access to the data unless explicitly entitled.

Precise Access Controls
Access to archive functionality and its underlying data is controlled by roles, and access to data is further controlled by custodian, data type, eDiscovery case status, time, device, and other attributes. Attribute-Based Access Controls (ABAC) give you much greater leeway to refine the circumstances under which data can be accessed than just Role-Based Access Controls (RBAC). Open APIs enable users to access and act on archive data from within leading applications such as Microsoft 365 and Exterro eDiscovery

Data Security and Multi-Level Entitlement Through Encryption
Vendors of most data management platforms control your tenant’s encryption keys. Some enable you to manage your tenant encryption keys yourself. Only Archive360’s Security Gateway enables you to manage the keys in an environment apart from your data in the cloud, so if hackers gain access to your data, they cannot decrypt it. It also enables you to control access to files and redact or mask specific fields through data classification-driven encryption.

Key Benefits of Archive360 Digital Communications Governance and Archiving
- Centralize communications and data governance at scale across organization systems
- Eliminate legacy email archive maintenance, infrastructure, and licensing costs
- Mitigate data security & privacy risks
- Ensure compliance with classification- and policy-based data retention, legal hold, and entitlements
- Account for all data, associated permissions, and actions with a complete chain of custody
- Facilitate data discovery by finding what you need in a single search or query across petabytes of data from multiple systems
- Save time and resources by giving your workforce secure, controlled self-service access to archived data
- Archive and manage all types of data from a wide range of systems
- Take advantage of Archive360’s seasoned expertise to complete the project efficiently, compliantly, and cost-effectively
- Create an evidence-grade communications record that supports investigations today and AI-era oversight tomorrow
CUSTOMER SUCCESS STORY
Top 3 Management Consulting Firm Centralizes and Streamlines the Governance of its Digital Communications While Adhering to Regional Data Sovereignty Requirements
“We needed a highly scalable and secure archive to capture all our communications around the world, processing and retaining data in the region it was created to meet GDPR requirements. Of all the archiving solutions we tested, Archive360’s platform was the only one that could meet our scalability and jurisdictional retention requirements.”
- Director, Cloud Engineering
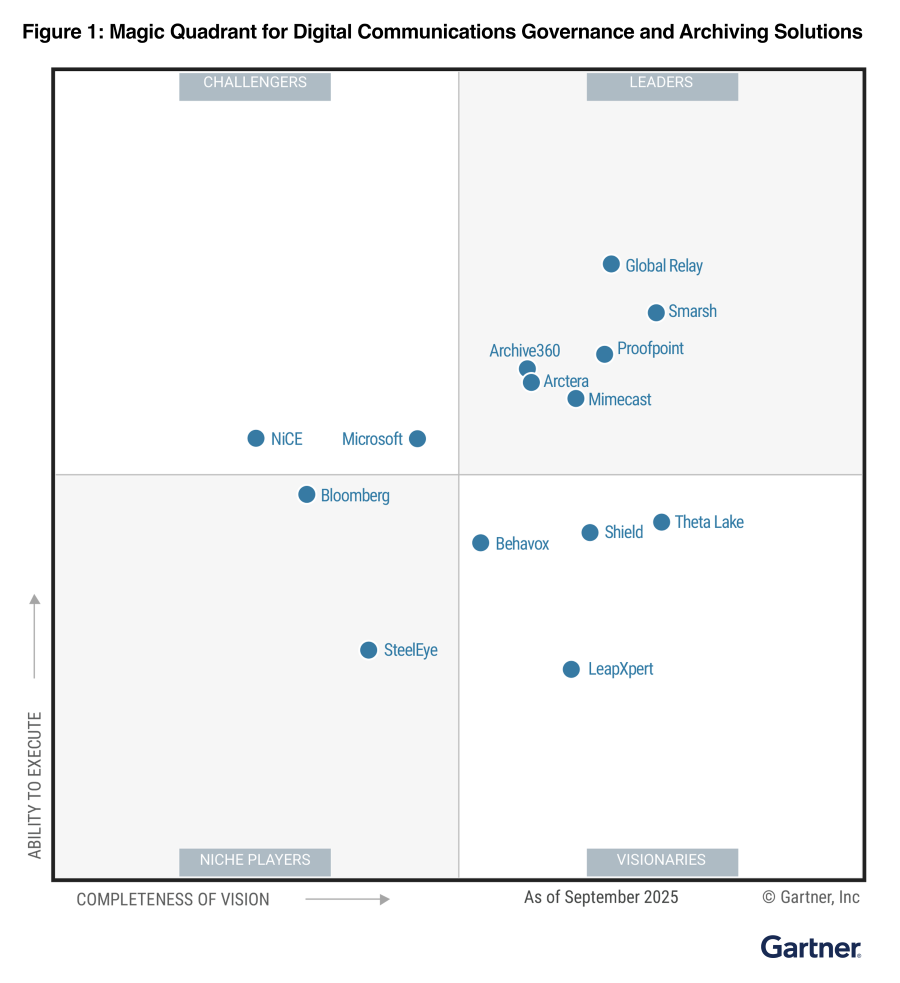
Analyst Report
A Leader in the 2025 Gartner® Magic Quadrant™ for Digital Communications Governance and Archiving Solutions
Get a demo
There are better solutions for migrating and governing all your data. Let’s discuss.



